From DD-WRT Wiki
Ch-server and astojanov-mac are behind the same router and are part of the 192.168.1.0/24 network. Note that the client astojanov-mac can access the OpenVPN server from any network node on the Internet. Thus the route to access the ch-server goes through the Internet cloud. OpenVPN allows VPN server to issue an authentication certificate to the clients. The exported file is a zip file that contains ca.crt (certificate file for VPN server), openvpn.ovpn (configuration file for the client), and README.txt (simple instruction on how to set up OpenVPN. OpenVPN Access Server is a full featured SSL VPN software solution that integrates OpenVPN server capabilities, enterprise management capabilities, simplified OpenVPN Connect UI, and OpenVPN Client software packages that accommodate Windows, MAC, and Linux, mobile OS (Android and iOS) environments. Installing and configuring an OpenVPN server manually is not a simple task from my.
English • Deutsch • Español • Français • Italiano • 日本語 • Polski • Português • Русский • Svenska • 中文(中国大陆) • 中文(台灣) • |
OpenVPN is a full-featured SSL VPN solution which can accomodate a wide range of configurations, including road warrior access, home/office/campus telecommuting, WiFi security, secure branch office linking, and enterprise-scale remote access solutions with load balancing, failover, and fine-grained access-controls.
|
Refer to OpenVPN documentation for details on all OpenVPN features:
Install the OpenVPN client on the computer: Windows, Mac
Please note that it consists of one binary for both client and server connections, they are not separate packages.
You will have several possibilities to authenticate to an openvpn session. Some authentication methods are supported by the gui directly (should be preferred), others have to be set up in daemon mode. Which you will use depends on some things: how secure, easy to setup, easy to maintain
[edit]Public Key Infrastructure (PKI) [Certificates]
Pro-Linux article (German) about PKI security (13 Sep 2013): Current state of cryptography [English translation]
Follow these instructions to create the required certificates and keys. But there is also a Webmin module for linux servers to create your PKI infrastructure (OpenVPN CA). You begin by creating a key and certificate pair for the certificate authority (CA) you are establishing. Then for the server and each client, you create a private key and certificate pair and sign the certificates using the CA's key. Afterwards, you should have the following files:
and a private key and certificate pair for each client. For example, if you have two clients, you should have:
Note: The CA private key (ca.key) is only to sign the certificates. Keep it secure and do not copy to the server nor clients.
OpenVPN certs must be generated with SHA auth: see this thread
[edit]Static Key
This method is only usable for connecting one client to a server!
On Linux you can create a pair of keys with:
For Windows, ensure openvpn is installed. To create a pair of keys go to:
Finally, copy the content of the keys to the ddwrt GUI static key field.
Also see: Static Key How-To and Create Static Keypair
Forum thread: OpenVPN server setup guide
This assumes DD-WRT with OpenVPN is installed on the router. OpenVPN is only available on units with at least 8mb flash (except the Broadcom VPN build). Instructions may vary based on version, as the following is for builds since 2011.
The DD-WRT GUI Server and Client modes' defaults should suffice for most users.
- Using the Web Interface, go to the 'Services' tab and then the 'VPN' tab (for older versions of dd-wrt go to the 'Administration' tab and then the 'Services' sub-tab).
- Enable OpenVPN Daemon or OpenVPN Client. If further options do not appear, click Apply Settings.
- Fill in needed parameters (see below). Everything else not mentioned here is taken care of automatically (e.g. firewall)
- Click Apply Settings.
Set up OpenVPN client where only specific traffic is routed via the VPN tunnel: Selective Routing Using DD-WRT & OpenVPN
[edit]CLI settings
[edit]Scramble Patch by clayface
These posts adds a patch to openvpn which introduces forms of scrambling to the packet payload of any OpenVPN connection.To use it you need both sides patched, server and client, and you introduce a new scramble password phrase in server and client config files
[edit]GUI: Client Mode
[edit]Fixed Parameters
There are default parameters that will always be written to the config file and which you cant change if you use GUI client mode:
[edit]Changeable Parameters
DD-WRT default settings in {}
OpenVPN config language in []
- Server IP/Name (e.g. 192.168.1.1)
- IP address/hostname of the OpenVPN server you want to connect to. [remote xxx]
- Port
- port which OpenVPN server is listening on. {1194} [port xxx]
- Tunnel Device (TUN/TAP)
- The mode of tunneling. TUN: routing (layer 3), TAP: bridgeing (layer 2. can be used for routing, too, but its not very common). [dev-type tun/tap]
- Tunnel Protocoll (UDP/TCP)
- The subprotocol the connection will use on the connection. {udp} [proto udp/tcp]
- Encryption Cipher (None and Blowfish to AES512)
- The encryption algorithm that will be used for the tunnel. Blowfish 'fastest' to AES512 'safest'. {AES128} [cipher xxx]
- Hash Algorithm (None and MD4 to SHA512)
- The hash algorithm that will be used. MD4: fastest (maybe unsafe) to SHA512. {SHA256} [auth xxx]
- Advanced options
- Leave defaults as is if you dont know what you are doing. {disabled} []
- TLS Cipher
- What encryption algorithm OpenVPN should use for encrypting its control channel. {disabled} []
- LZO Compression
- Enables compression over VPN. This might speedup the connection. Must be the same value as on server. {adaptive} [comp-lzo yes/no/adaptive/disabled]
- NAT
- Enable network address translation on the client side of the connection. Enables the NAT-firewall to protect clients. {disabled}
- Bridge TAP to br0
- Enable a transparent bridge across the tunnel to the local LAN. Works only in TAP mode with NAT disabled. {disabled}
- Local IP Address
- In cases you will not get an ip from the server. Not very common. {empty)
- Subnet Mask
- Subnet Mask for the IP Address.
- TUN MTU Setting
- set the mtu of the tunnel {1500} [tun-mtu xxx]
- UDP Fragment across the tunnel
- set mss-fix and fragmentaion accross the tunnel. {empty} [fragment xxx]
- UDP MSS-Fix
- = value of Fragment. Only usen with udp. should be set on one side only. [mssfix]
- nsCertType verification
- Checks to see if the remote server is using a valid type of certificate meant for OpenVPN connections. As this is a security feature of OpenVPN, it should be left enabled. {checked} []
- TLS Auth Key
- The static key OpenVPN should use for generating HMAC send/receive keys. {disabled} []
- Additional Config
- Any additional configurations you want to define for the VPN connection. {empty}
- Policy based Routing
- allow only special clients to use the tunnel. Add IPs in the form 0.0.0.0/0 to force clients to use the tunnel as default gateway. One line per IP. {} []
- Public Server Cert
- Certificate of OpenVPN CA (not the server's public cert) in pem form; only part between (and including) -----BEGIN CERTIFICATE----- and -----END CERTIFICATE----- is necessary; as it is stored in nvram, everything else from that file should be removed to conserve space.
- CA Cert
- CA certificate; also only part between 'BEGIN' and 'END' is required.
- Private Client Key
- Key associated with certificate above; should be kept secret because anybody who knows this key can successfully authenticate as this client.
- DH PEM
- Diffie Hellmann parameter.
- Static Key
- used for p2p links. No pki needed.
[edit]GUI: Server Configuration
This section describes how to configure an OpenVPN server that uses SSL certificates for client authentication, which is recommended. The method offers better security than using a static key and allows multiple clients to connect at the same time.
[edit]Fixed Parameters
There are default parameters in the DD-WRT config file that cannot be changed using the GUI server mode:
[edit]Customizable Parameters
DD-WRT default settings in {}
OpenVPN config language in []
- Start Type
- use 'System'. 'WAN Up' doesnt work. {}
- Config via (GUI/config file)
- GUI {}
- Server Mode (TUN/TAP)
- The mode of tunneling. TUN: routing (layer 3), TAP: bridging networks (layer 2). {} [dev-type tun/tap]
- DHCP-Proxy mode
- Only in bridge mode. Let the clients use the network dhcp server not the openvpn dhcp. {} []
- Pool start Ip
- 1st ip of the ip pool used (Only in bridge mode). []
- Pool end IP
- Last ip of the ip pool used (Only in bridge mode). []
- Gateway
- Default gateway to use (Only in bridge mode). []
- Network (e.g. 10.10.10.0)
- Network to use for the tunnel (Only in routing mode). []
- Netmask (e.g. 255.255.255.0)
- Netmask of the used network. []
- Block DHCP accross the tunnel
- Dont allow DHCP requests across tunnel (Only in bridge mode).
- Port
- port which OpenVPN server listens on. {1194} [port xxx]
- Tunnel Protocoll (UDP/TCP)
- The subprotocol the connection will use on the real used tcp connection. {udp} [proto udp/tcp]
- Encryption Cipher (None and Blowfish to AES512)
- The encryption algorithm that will be used for the tunnel. Blowfish: fastest to AES512 safest. {AES128} [cipher xxx]
- Hash Algorithm (None and MD4 to SHA512)
- The hash algorithm that will be used. MD4: fastest (maybe unsafe) to SHA512. {SHA256} [auth xxx]
- Advanced options
- Leave defaults as is if you dont know what you are doing. {disabled}
- LZO Compression
- Enables compression over VPN. This might speedup the connection. Must be the same value as on server. {yes} [comp-lzo yes/no/adaptive/disabled]
- Redirect default Gateway
- Force the clients to use the tunnel as default gateway. {disabled} []
- Allow Client to Client
- Allow clients to see each other. {disabled} [client-to-client]
- Allow duplicate cn
- allow to use 1 client cert to use on multiple clients (security risc)
- TUN MTU Setting
- set the mtu of the tunnel {1500} [tun-mtu xxx]
- MSS-Fix/Fragment across the tunnel
- set mss-fix and fragmentaion accross the tunnel. {empty} [fragment xxx] [mssfix]
- TLS Cipher
- What encryption algorithm OpenVPN should use for encrypting its control channel. {disabled} []
- TLS Auth Key
- The static key OpenVPN should use for generating HMAC send/receive keys.
- Client connect script
- . {empty} []
- Additional Config
- Any additional configurations you want to define for the VPN connection. {empty}
- CA Cert
- Certificate of OpenVPN CA in pem form (usually ca.crt); only part between (and including) -----BEGIN CERTIFICATE----- and -----END CERTIFICATE----- is necessary; as it is stored in nvram, everything else from that file should be removed to conserve space.
- Public Server Cert
- Server certificate issued by CA for this particular router (usually server.crt); also only part between 'BEGIN' and 'END' is required.
- Private Server Key
- Key associated with certificate above (usually server.key); should be kept secret because anybody who knows this key can successfully authenticate client certificates.
- DH PEM
- Diffie Hellman parameters generated for the OpenVPN server (usually dh1024.pem).
[edit]Authentication with username and password
Certificates are nice, but having usernames and passwords can complement certificates. You can use the following scripts below to check for usernames/passwords.
Add this to the config on the server and set the right path for the script:
The script-security line is to resolve the issue where an external program may not be called due to setting of --script-security levelThe auth-user-pass-verify line enables the OpenVPN server to check the passed username and password by calling the script verify.sh and passing the username and password in a tmp file.
Every client will need to have this in its config file to connect:
This tells OpenVPN client to ask the user for username and password or s/he will not be able to log in. You can also use '--auth-user-pass' (instead of the line in the config file) on the command line.
I have split up the functions into separate files compared to predecessors (See page history).The verification done by the script may not work if OpenVPN is running in 'daemon' mode (to be confirmed).
[Edit by Rocketboy235 Jan 21 2020]The script below has been updated to make use of SHA1 checksum instead of MD5 since the last time I created it back in mid 2018. However, SHA1 has been cracked since early 2019 so hopefully dd-wrt will come packaged with a more secure/newer hash tool that can be used. Also added instructions on how to setup the scripts for OpenVPN login authentication.
Instructions on how to use the below scripts
Add both scripts to your router and make sure to do chmod +x for each file.Then you can run Genhash.sh and pass the username and password arguments.
Example:
./genhash.sh NameOfMyUser MyLovelyPassword
This will generate a users file in /tmp and you can move it to whereever you like but you will need to update the Verify.sh script (line 14 ( begins with 'users=' )when you copy/paste this script) so that it points to that file when looking at the user list. For example, I place these scripts and my users file in /jffs/etc/openvpn/. Just note that if you save stuff in /tmp, you will lose them when the router reboots or loses power.
Verify.sh
Genhash.sh
[edit]Client Configuration
1) Copy the CA certificate and a private key and certificate pair to the client.
2) Create an OpenVPN configuration file on your client computer:
Replace router-address in the fourth line with your router's IP address or host name and, obviously, use the appropriate file names in the script for the client's certificate and key. On Windows, save this script using notepad as a file with extension .ovpn and copy it into Program FilesOpenVPNconfig (along with the files ca.crt, clientX.crt and clientX.key created earlier.)
Notes:
- If you need to use TCP instead of UDP, set the protocol to tcp-client. Clients must use the same protocol that the server does.
- Client config also need match these server parameters: dev (tun/tap), cipher, auth, comp-lzo, tun-mtu.
- Mac OS X users and Linux users using TAP need to add the line
to the configuration file and create a script file vpn-up.sh in the same directory as the configuration file with the following contents.
On Mac:
On Linux:
This script configures the TAP interface to request an IP address using DHCP. Make sure to make the script executable with 'chmod 755 vpn-up.sh'.
3) Use the configuration file you just created with whatever OpenVPN client software you're using to establish a connection to your router.
If everything works, you will be connected to your internal LAN. If your router is running a DHCP server, the TAP interface will be assigned an IP address on your internal LAN. At this point, you just connect to your home PC the same way you would do it from inside your LAN.
[edit]Daemon Mode/Config File
Bridge 2 Networks
Route 2 Networks
[edit]FAQ
[edit]MTU
One verycommon problem is the wrong setting of the mtu/fragment/mss-fix values. Ethernet's max frame size is 1500. In most cases where the Router is the gateway and the vpn connects to the outside world the values must be changed. WAN connections in general will have a lower frame size so the default setting will result in a dropping connection. mtu/fragment must be set the same on both sides!
On tcp connections only mtu can be set. Try setting the mtu to 1300 and see if it works.
On udp connections enable mss-fix on one side of the link. Lower the fragemt size to 1300 and try if its working.
In both cases when the link is working u can try to raise the values again to the maximum which will be working.
[edit]Logs
logs are written to syslog and can be seen in the GUI: Status -> OpenVPN (not in daemon and script mode)
[edit]Correct time
OpenVPN requires client and server to have more or less synchronized time. Therefore make sure that router has correct time. To check it use command date and if you get info about year 1970, you should enable NTP client. Also, ntp server has to be outside of your VPN as time should be corrected before VPN is established. If you have syslog enabled (to local server, or the server outside your VPN), errors like TLS Error: Unroutable control packet received from server_ip:1194 may indicate this problem. (This error message may appear if your certificates are not valid or have expired, too.)If you get an error message saying that your certificate is not yet valid, set the dd-wrt clock to UTC time (in the first configuration page).
To set the time manually connect via telnet or ssh and issue the following command at the prompt:
date MMDDHHMMYYYY
[edit]Connecting to DD-WRT OpenVPN Server via Mac Client
Currently, there are two OpenVPN clients for OS X
Viscosity has a more user friendly GUI but is a commercial product. It can also import settings created for the Tunnelblick application.
PROBLEM: When I used the sample client.conf file above, nothing happened when I clicked connect on Tunnelblick.
Tunnelblick is a GUI OpenVPN application for the Mac. The last official release is 2.0.1, but I am going to explain how to connect using version 3.0rc3. This version has everything in one app and requires no extra components to be installed.
NOTE: I used certificates to connect my MacBook Pro to the OpenVPN server. You can find documentation on how to do this further up in this page. Remember to place your certificate files in the same directory as the client.conf file. Tunnelblick looks for the files in ~/Library/openvpn.
Download Tunnelblick and drag it to the Applications folder. It will say that you don't have a client.conf file and will make one for you. You can examine the sample client.conf file that Tunnelblick makes and find that it does a few things differently than the example provided above. Set up your client.conf file using the sample I have provided below, and Tunnelblick should connect properly now.
The file I have provided is the same as the sample, except with a few things disabled and a few things added to make it do what we want. The reason I disabled a few things using the # line is that I didn't want to delete anything, so I just disabled them.
You might notice that the command
This is a fix that I found here.
You will need to make a script called vpn-up.sh and place it in the same directory as the client.conf file. Make the files contents:
client.conf:
UPDATE Sept 1, 2009
The most recent release of Tunnelblick is 3.0rc14. It seems as though the previously mention bash script does not work anymore. The following python script does work, however:
[edit]Can't Load DH Parameters
If you get the following:
you should check your certificates. Did you paste them correctly?
Note: you must include new lines.
[edit]Connection reset by peer (WSAECONNRESET) (code=10054)
If you received error when trying to connect to your VPN server verify the following:
- Make sure the tap-device was successfully 'up'ed'. It is, if you find it in the list when running 'ifconfig' without further arguments. If it is not displayed in the list of available interfaces have a look at 'Yet another evolution' above.
- Make sure the protocol is the same on the server and client, ie UDP/TCP
- Verify the port number is the same on the client and server; Default port is UDP 1194
- Check to see if the port is open on the server by using nMap or another utility
[edit]Incoming Packet Rejected
If you get incoming packets being rejected when trying to connect with the VPN client (OpenVPN) make sure that you are forwarding the 1194 port (if configured to use that port) to the proper server/router (usually 192.168.1.1).
Example TCP/UDP Rejection:
- [Date] TCP/UDP: Incoming packet rejected from 192.168.1.1:1194[2], expected peer address: w.x.y.z:1194 (allow this incoming source address/port by removing --remote or adding --float)
Port Forwarding is configured on v24 SP 2 under 'NAT / Qos'.
[edit]Authenticate/Decrypt failure
If this happens to you, you probably have a mismatch in the configuration between server and client on the 'cipher'-option. (E.g.: cipher AES-128-CB / cipher AES-256-CB)This is not a problem of DD-WRT or OpenVPN but just a config issue which can happen if you follow some of those guidelines strictly without knowing what the config options mean.
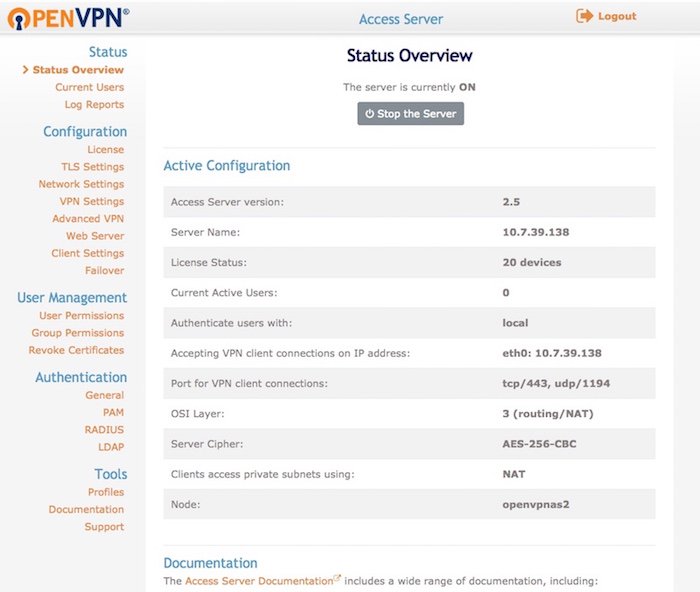
This is my 1st time install and run OpenVPN Access Server.
OpenVPN Access Server: Ubuntu 16.04 LTS (32bit)
I have my server behind a router. The server is updated with Dyndns account via' ddconnect'. All is good and I use the default settings of the OPVN-AS
Openvpn Server For Mac High Sierra
Client: MacOS with OpenVPN connect for MAC installed.I can access other devices on the VPN network, no problem here.
But when I try to access the Internet, say for example, go to http://www.apple.com --> The browser throws error, time out. Status shows that it was trying to 'resolve host' but did not succeed I guess.
My question is, how can I enable Internet access for the clients?
Openvpn Mac Free
Thank you very much for your support